
Git Workflow for YAML API Tests: PR Checks, Reports, Merge Rules
When API tests live outside Git, your merge gates are basically guesses. The hard part is not “writing tests”, it’s making them behave like production code: reviewable diffs, deterministic runs, and merge rules that keep the main branch green.
A YAML-first workflow (where tests are committed as native YAML, not a UI export or custom DSL) maps cleanly onto standard Git practices: PR review, required checks, artifacts, and merge queues. This post focuses on the mechanics: what to require in PRs, what to report, and how to encode merge rules that scale.
The core idea: treat API tests like code, not like tool state
A Git workflow for API tests is primarily about two things:
- Reviewability: PR reviewers can understand what changed and why.
- Determinism: CI results reflect real behavior, not environment drift or hidden client behavior.
This is where YAML-based API tests are a practical advantage over Postman/Newman and many UI-centric tools.
- Postman collections are JSON exports of a tool state, diffs are often noisy, and logic tends to migrate into scripts.
- Newman runs those collections in CI, but you are still reviewing an exported artifact.
- Bruno is closer to “tests as files”, but it still relies on its own format and conventions rather than native YAML that your team already lints, formats, and reviews elsewhere.
With DevTools, flows are committed as native YAML that can be reviewed in pull requests and executed locally or in CI via a CLI runner.
Repo conventions that make PRs boring (in a good way)
The goal is to keep diffs small, make ownership explicit, and stop test changes from leaking into unrelated PRs.
A layout that tends to work well:
flows/for the YAML flows you execute in CIenv/for environment templates (non-secret defaults)fixtures/for stable payloads and golden filesscripts/for CI glue code (report conversion, summaries)
If you already have a monorepo, keep the same idea but scope it (for example services/payments/api-tests/flows/).
Add CODEOWNERS for test gating
If API tests protect production, treat them as protected code paths:
- Make changes to
flows/**require review from API owners or SDETs. - Block “drive-by” edits that weaken assertions.
GitHub CODEOWNERS is the simplest enforcement mechanism. GitHub branch protection can then require CODEOWNER review.
What to run in PRs vs what to run after merge
PR checks should be fast and actionable. Post-merge checks can be heavier. This is less about “test types” and more about merge economics.
A useful split:
| Check | Runs on | Goal | Merge rule guidance |
|---|---|---|---|
| Smoke flow suite | PR | Catch obvious breakage quickly | Required |
| Contract assertions (schemas, headers) | PR | Catch incompatible changes | Required for API repos |
| Full regression suite | Scheduled and main | Catch slow integration regressions | Not required (usually), but alerts and rollback gates |
| Rate-limit and retry behavior | main | Validate resilience without slowing dev loop | Optional required in high-risk systems |
The important part is not the label, it’s making checks predictable:
- PR checks should run against an environment that is stable enough to be meaningful.
- If your staging environment is shared and flaky, consider a dedicated CI environment or ephemeral environments per PR.
Reporting: what reviewers need to see in the PR
You want reviewers to answer these questions without opening CI logs:
- What failed?
- Which request step failed?
- What assertion failed?
- Is this a product bug, an environment issue, or a test issue?
For CI systems, JUnit remains the lowest-friction format because it integrates with test UIs, annotations, and history in most platforms.
DevTools supports generating reports (including JUnit and JSON). In a GitHub workflow, the practical pattern is:
- Emit JUnit for inline “test failure” UX.
- Upload the richer JSON report as an artifact for debugging.
- Add a short PR summary (counts, links to artifacts, top failures).
If you are used to Newman, this is the same intent as its reporters, but without the collection export problem and with YAML flows that stay readable in Git.
PR summaries should be stable, not verbose
A CI summary that changes ordering every run trains engineers to ignore it. Prefer:
- A fixed ordering (by flow file path, then by step id)
- A small “Top failures” section
- A link to artifacts
If you need flake investigation, store the details in artifacts, not in the PR comment.
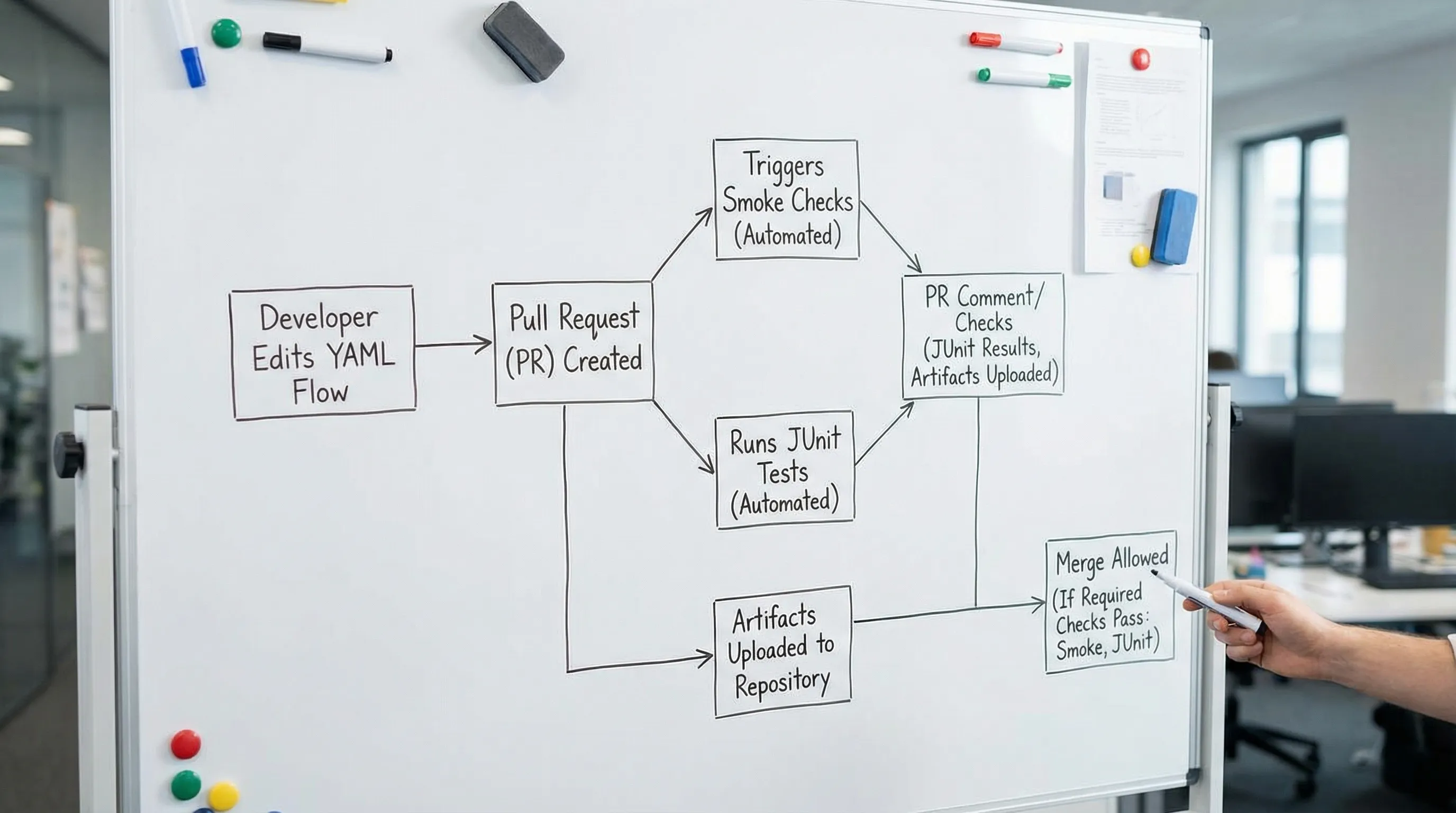
Merge rules that actually protect you
Branch protection is the contract between “tests as code” and “tests as gate”. For GitHub, the features you care about are:
- Required status checks
- Required pull request reviews
- CODEOWNER review requirement
- Merge queue (for high-traffic repos)
GitHub’s docs on required status checks and merge queues are worth reading if you have not tuned these before.
Recommended protection settings for API test repos
These settings tend to work well for teams that want strictness without deadlocking themselves:
- Require PR review (1 or 2 approvals)
- Require CODEOWNER review for
flows/** - Require status checks:
- lint or validation (fast)
- smoke suite (fast)
- contract suite (fast)
- Require branches to be up to date before merging (especially if you are not using a merge queue)
- Restrict who can push to main
If you use a merge queue, keep the required set tight. The queue can run the same checks against the merge commit, which reduces “green PR, red main”.
YAML flow patterns that make diffs reviewable
A PR workflow only works if diffs are stable. The two biggest sources of review pain are:
- Unstable serialization or noisy formatting
- Tests that rely on transient headers, timestamps, randomized IDs, or non-deterministic ordering
DevTools’ YAML-first approach helps because reviewers are reading the same file that runs in CI, not a generated collection export.
Keep request chaining explicit
Request chaining is where UI tools often hide complexity: token capture, ID propagation, correlation, and environment switching. In YAML, you want this explicit so PR reviewers can see the data flow.
Here is an illustrative (simplified) flow showing the pattern, not a tool-locked script. The important pieces are: capture outputs, reuse them, and assert on stable contracts.
id: payments-smoke
vars:
base_url: ${BASE_URL}
steps:
- id: auth
request:
method: POST
url: ${base_url}/oauth/token
json:
client_id: ${CLIENT_ID}
client_secret: ${CLIENT_SECRET}
extract:
access_token: $.access_token
assert:
status: 200
- id: create_charge
request:
method: POST
url: ${base_url}/charges
headers:
Authorization: Bearer ${access_token}
json:
amount: 499
currency: USD
extract:
charge_id: $.id
assert:
status: 201
jsonpath:
- path: $.currency
equals: USD
- id: get_charge
request:
method: GET
url: ${base_url}/charges/${charge_id}
headers:
Authorization: Bearer ${access_token}
assert:
status: 200
jsonpath:
- path: $.id
equals: ${charge_id}
Even if your exact schema differs, the review principle stays the same: chaining should be obvious in the diff.
Prefer contract assertions over incidental assertions
Avoid asserting on:
Dateheaders- server-generated UUIDs you do not capture and reuse
- ordering of arrays unless the API contract guarantees ordering
Prefer asserting on:
- status codes
- required headers (
Content-Type, caching semantics) - schema invariants
- id propagation (capture once, compare later)
This is where YAML flows tend to be clearer than Postman script assertions because the intent is declarative, and reviewers do not have to interpret ad hoc JavaScript.
CI integration without tool lock-in
In practice, a good CI job does four things:
- Pull the repo
- Provide environment variables (base URLs, credentials)
- Run the CLI test runner
- Publish reports and artifacts
DevTools is explicitly designed to run locally and in CI, so you can keep the “source of truth” in Git and avoid special cases where only a desktop app can execute the suite.
If you want a concrete GitHub Actions starting point for running YAML flows and uploading JUnit artifacts, the DevTools guide on API regression testing in GitHub Actions is the copy-paste baseline. In this post, the emphasis is the workflow design: which checks you require and how you enforce merges.
Use the same command locally and in CI
A common failure mode with Newman and UI-based tools is drift between “what devs run locally” and “what CI runs”. Enforce parity:
- The same flow files
- The same environment variable contract
- The same report outputs
If developers can run a single CLI command locally before pushing, PR checks become confirmation rather than discovery.
Handling flaky tests without weakening merge gates
If you start requiring checks, you will surface flakes. That is good, but only if you have a policy.
A pragmatic approach:
- Retries are allowed only for known transient classes (timeouts, 429s), and should be explicit.
- No global “retry everything” in PR checks, it hides real failures.
- Quarantine is time-boxed: if you skip a flow, it must be tracked and removed from quarantine quickly.
If your organization needs a mental model, treat flaky tests like failing lint: you do not “accept” the failure, you fix the system that produces it.
Comparing Git-first YAML workflows to Postman/Newman and Bruno
This is not about which tool can “send requests”, they all can. It’s about what you can reliably enforce in PRs.
Postman and Newman
- PR diffs are against exported collections and environments, not against the actual edit intent.
- Test logic often lives in scripts, which are harder to standardize and review.
- Environment handling can become a parallel configuration system rather than Git-native configuration.
Newman is fine as a runner, but it does not change the fact that your tests are authored inside a UI and serialized into tool-specific JSON.
Bruno
Bruno’s file-based approach is closer to the Git mindset, but you still adopt a separate format and conventions. For teams already standardizing on YAML for infra and automation, native YAML keeps everything in the same tooling universe (linters, diffs, review habits).
DevTools
DevTools’ differentiator in this comparison is straightforward: flows are native YAML, generated from real browser traffic when needed (HAR capture), and executed locally or in CI via a CLI runner.
If you are migrating, DevTools also has a practical guide to migrate from Postman to DevTools, which is useful when you want to keep your existing coverage but move the source of truth into Git-reviewed YAML.
Practical scenario: third-party API checks as merge gates
Third-party integrations break in two ways: you change your client code, or the provider changes behavior. A Git workflow for API tests should cover both.
For example, if your product automates outbound messaging or lead qualification, you might depend on external automation services. When evaluating vendors (for example Orsay for AI-driven Instagram outreach and lead follow-up), you can write YAML flows that validate:
- auth and token refresh behavior
- rate limit responses and backoff behavior
- required fields and validation error shapes
The point is not to “test the vendor”, it’s to lock down your integration contract so changes in your codebase cannot silently break it.
Frequently Asked Questions
What status checks should be required for YAML API tests? Require fast checks that catch real breakages: a smoke suite, contract assertions, and basic validation (lint or schema validation). Keep full regression as post-merge or scheduled unless your repo is small.
How do you make PR reports useful without dumping logs into the PR? Emit JUnit so failures show up inline, and upload richer artifacts (for example JSON reports, request/response traces with secrets redacted). Keep PR summaries stable and short.
Should we use a merge queue for API test repos? If your main branch sees frequent merges and you get “green PR, red main”, a merge queue is often worth it. It runs checks on the merge commit and reduces integration races.
How do YAML flows help with code review compared to Postman collections? YAML is human-readable and produces cleaner diffs. Reviewers can see exactly which request, assertion, or chained variable changed, without reverse-engineering an exported collection.
How should we handle secrets in Git workflows for API tests? Keep secrets out of YAML, inject them via CI secrets or environment variables, and prefer request chaining to fetch short-lived tokens. If your suite starts from HAR captures, redact aggressively before anything leaves a developer machine.
Run API tests like code with DevTools
If your current workflow relies on Postman/Newman exports or UI-authored tests, moving to Git-reviewed YAML is usually the biggest quality jump you can make. DevTools is built for that: capture real traffic when you need it, commit readable YAML flows, and run them locally or in CI.
Start with DevTools at dev.tools, then wire your branch protection to require the smoke and contract checks that match your team’s risk tolerance.